Private Equity investors, C-suite executives, and board members are familiar with the high-stakes decision-making required to operate businesses, make deals, and innovate.
But when it comes to cybersecurity, these groups often push policy and technology decisions to their IT teams. In today’s environment, where U.S-based cyber breaches are costing businesses ~$8.64 million in remediation, senior executives must recognize that the responsibility is not only on CIOs, but the entire C-suite and board.
Why Cybersecurity is the Responsibility of the C-Suite and the Board
According to recent research by the Poneman Institute and IBM, 1 in 4 people now hold the CEO/COO responsible for cybersecurity and technology decisions.
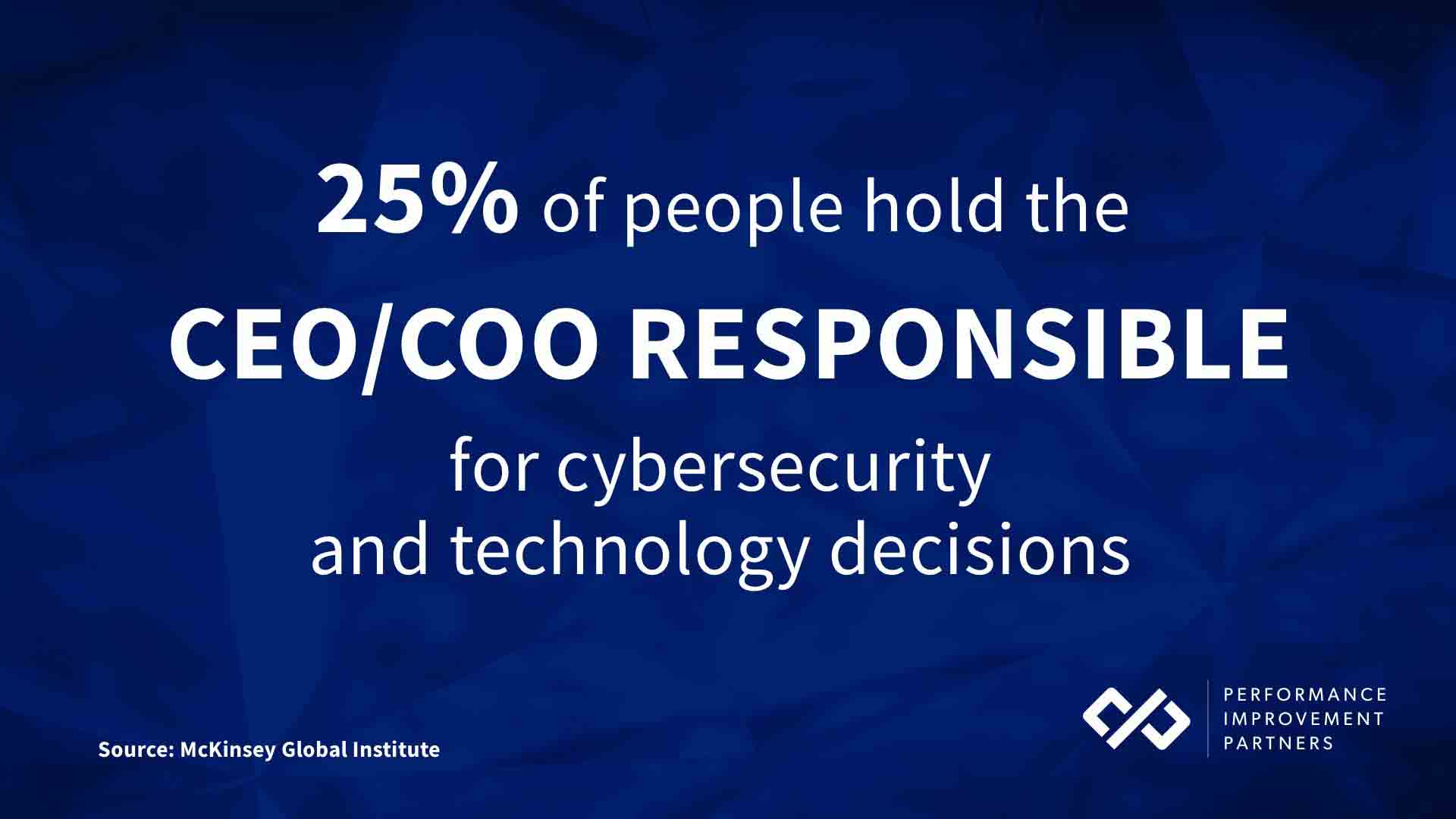
With cyber threats also now the number one concern for investors, the stakes are simply too high for business leaders to continue to de-prioritize cyber protection – and unfortunately, ensuring cyber protection is more than a “one and done” effort.
Take Marriott, for example. Just last week the hotel group was slapped with a class-action lawsuit following a series of breaches on its reservation systems. As a result, Marriott faces millions in legal fees and fines, as well as a number of lawsuits (including GDPR), a loss in customers, and significant reputational damage. Following its 2018 data breach, CEO Arne Sorenson had to testify before Congress, and because their systems were breached yet again in March 2020, it wouldn’t be surprising to see him back in D.C. soon.
Private Equity is Quickly Becoming a Top Target for Cyber Attacks
When the COVID-19 pandemic hit in March, businesses were forced to close offices and deploy remote, virtual workforces. And as a result, cyber hackers almost immediately fired up their engines and began preying on the fears and emotions of employees on both a personal and professional level, targeting businesses at a 300% faster rate than pre-pandemic.
As major banks and hedge funds have invested extensive time and money into the software, hardware, and employee training needed to keep their investments protected, Private Equity firms have not, and hackers are taking notice of their deep pockets and, oftentimes, loose security systems.
In April, three British Private Equity firms were tricked into wiring ~$1.3 million to hackers – funds that were meant to be distributed to the bank accounts of the companies they were investing in. And as pandemic-related cyber activity continues, it’s predicted that 1 in 4 middle-market firms will experience a breach in the next year.
TIP: Understand the responsibility and liability of the C-Suite, Board, and Private Equity investors with the 2020 Guide to Cybersecurity.
Preparing for a Cyber Pandemic with the Defense in Depth (DiD) Approach
According to experts, cyber activity will only increase throughout the pandemic. Based on the latest cybersecurity statistics, the issue will only become bigger in scale for firms and corporations large and small, and therefore their executive teams and boards.
But the good news is, there are immediate steps that PE firms and their portfolio companies can take for protection and remediation, following the best-in-class Defense in Depth (DiD) approach, made up of four steps.
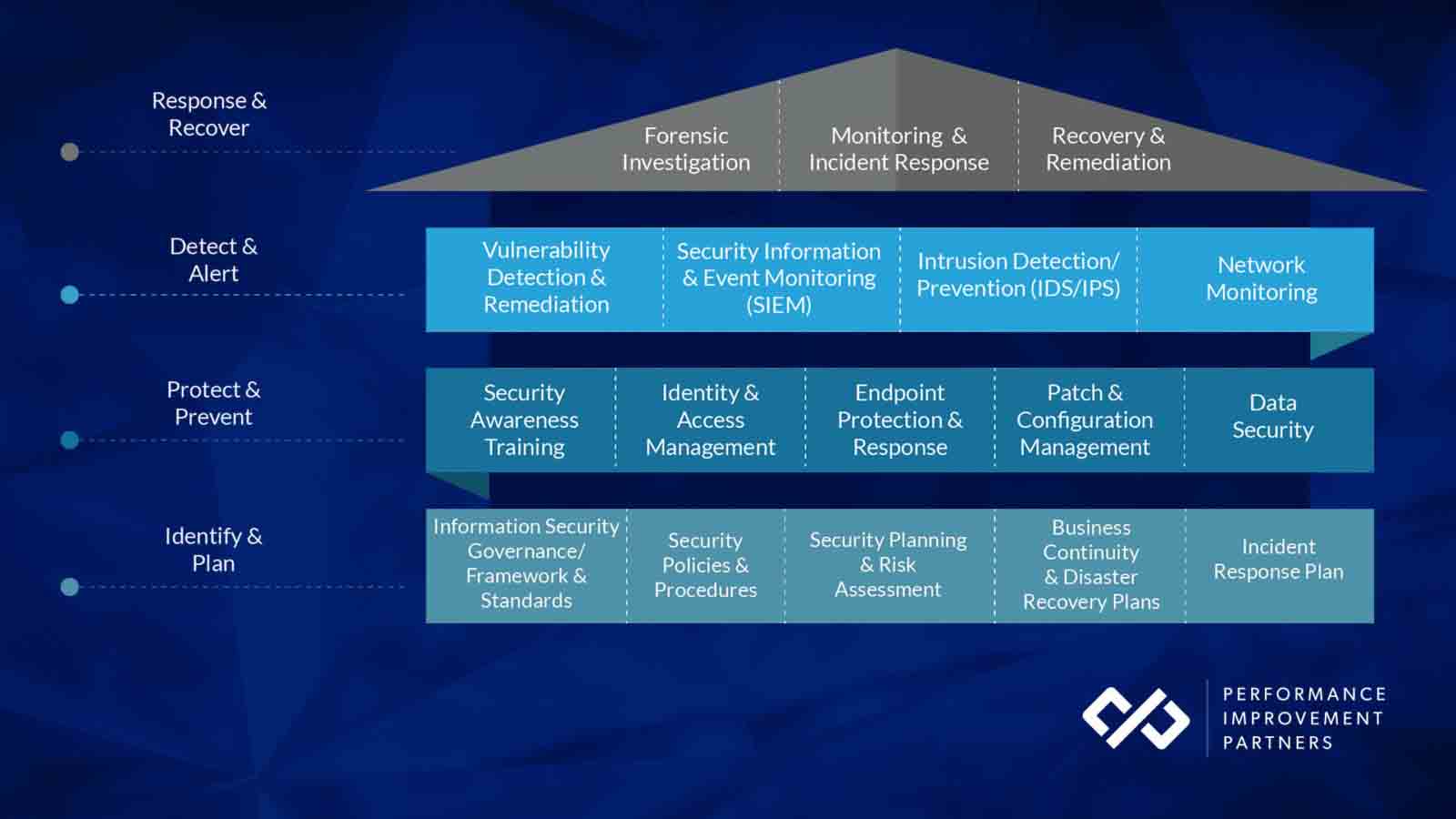
Many executives don’t consider their role in cybersecurity until they reach the top of the pyramid, after an incident has occurred. However, the technology impacts of COVID-19 has proven its necessary in maintaining business continuity.
To ensure effectiveness, leadership must be involved all stages of the Defense in Depth approach. Without laying the groundwork in the first two stages – planning and protecting – companies will be unable to efficiently respond and minimize losses following an attack.
Step one: Identify and Plan
The foundation of the Defense in Depth approach requires the creation of cybersecurity policies for all employees, in addition to an assessment of the company’s current state of cybersecurity to identify vulnerabilities in all systems. Once those steps are complete, it’s critical to develop an incident response plan with clear action items to take post-attack, which can save companies ~$2 million.
TIP: Identify cyber strengths and vulnerabilities within your portfolio with a personalized cybersecurity workshop. Recognized by ACG Middle Market Growth, your complimentary workshop is designed exclusively for Private Equity firms and their portfolio companies.
Step two: Protect and Prevent
At the second level of Defense in Depth, companies must implement standard security measures such as identify and access management tools, endpoint protection, and employee training – a vital element to protection, as 90% of attacks are due to human error and often lead to various issues that may impact cash flow. Other preventative measures include securing workstations (both in-office and remote), requiring the use of VPNs, multi-factor authentication (MFA), and anti-virus software. These measures are imperative to ensure cybersecurity with a remote workforce.
Step three: Detect and Alert
Following security practices mitigates risk. However, there is no immunity when it comes to cyber attacks as criminals are consistently evolving their methods. Regular system monitoring is a must in detecting attacks, and vulnerability scans should be conducted quarterly – at a minimum.
Step four: Respond and Recover
In the event of a breach, reacting quickly is essential. Immediate action items include securing systems, fixing identified vulnerabilities, and searching for exposed company data on the internet. In addition, companies should source cybersecurity professionals to assess the situation, identify immediate areas for remediation, negotiate the ransom, and consult legal counsel. Customers – both affected and unaffected – also need to be informed of the breach with guidance around remediation steps being taken, and that they need to take.
Leadership’s Prioritization of Cybersecurity Starts Now
As Nicholas David and Algirde Pipikaite with the World Economic Forum recently wrote, “COVID-19 is not the only risk with the ability to quickly and exponentially disrupt the way we live. The crisis shows that the world is far more prone to disturbance by pandemics, cyberattacks or environmental tipping points than history indicates. Our ‘new normal’ isn’t COVID-19 itself – it’s COVID-like incidents. And a cyber pandemic is probably as inevitable as a future disease pandemic. The time to start thinking about the response is – as always – yesterday.”


